Buy Instagram accounts cheap
🛒 Account store from 🐻 Grizzly SMS – 🔗
Instagram is one of the most popular social networks in the world. The number of users has exceeded several billion people. It's not only the perfect place to chat or post your photos. The service offers huge opportunities for promotion. It is not difficult to monetize an audience or engage in promotion. Almost all companies and organizations have a profile. To buy an Instagram account is a popular request. Let’s try to understand in more detail its features.
Why you need to buy an Instagram profile
Your own profile will not always be enough. A request to buy an Instagram account for an ordinary person occurs in the following situations:
- creating an anonymous account not associated with anything;
- use of an additional profile for personal purposes;
- separation of personal and business accounts.

A completely different situation arises when doing business. You need to buy an Instagram account with followers or an empty one for promotion. This allows marketers to make promotions and increase interest in certain products or services. Several profiles can create the appearance of a heated discussion or perform other tasks.
Often there is a request to buy Instagram accounts for mailing. The system actively monitors and bans them. We have to regularly acquire new ones.
How to buy an Instagram account cheap using the Grizzly Sms service
It should be said that the site offers an alternative approach. As mentioned earlier, you are not purchasing a social media account but rather a virtual number for Instagram verification. It is used to register. This method has a number of advantages, which will be discussed later. Here are step-by-step instructions on how to buy a verified Instagram account using a fake phone.
- You should start by registering an account on the “Grizzly Sms” website. This is required to make purchases. An email is being used. There is a faster way - registration in one click by importing data from social networks (Vkontakte, Instagram or Facebook).
- In the upper menu, select "Top up balance".
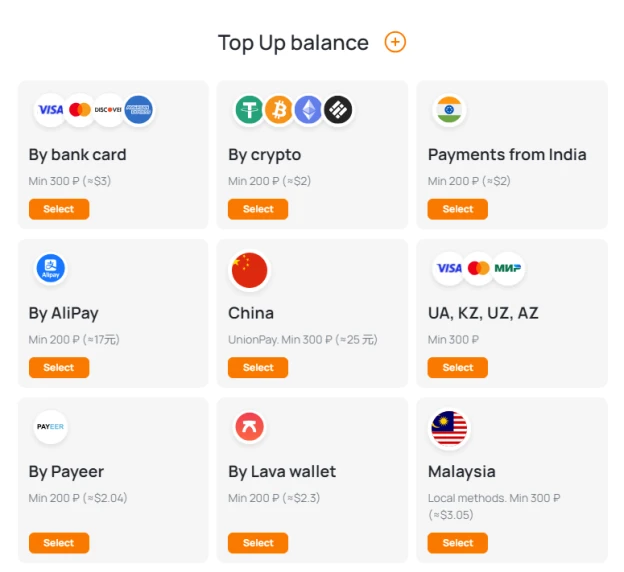
- You need to use one of the proposed payment methods. Choose from Visa / MasterCard bank cards, Google Pay / Apple Pay systems and cryptocurrency of the Payeer electronic wallet. When the option of interest is indicated, a window for entering the amount appears. It must be at least a few euros. Each of the payment methods contains information about the amount of the commission.
- You can buy a virtual number. Go to the store, where you first select the service and then the country. The system gives matches. The description indicates the number of available phones and the price per one. If the cost does not suit you, you can change the country. For bulk purchases, a discount is provided. To receive it, contact the manager through the feedback form.
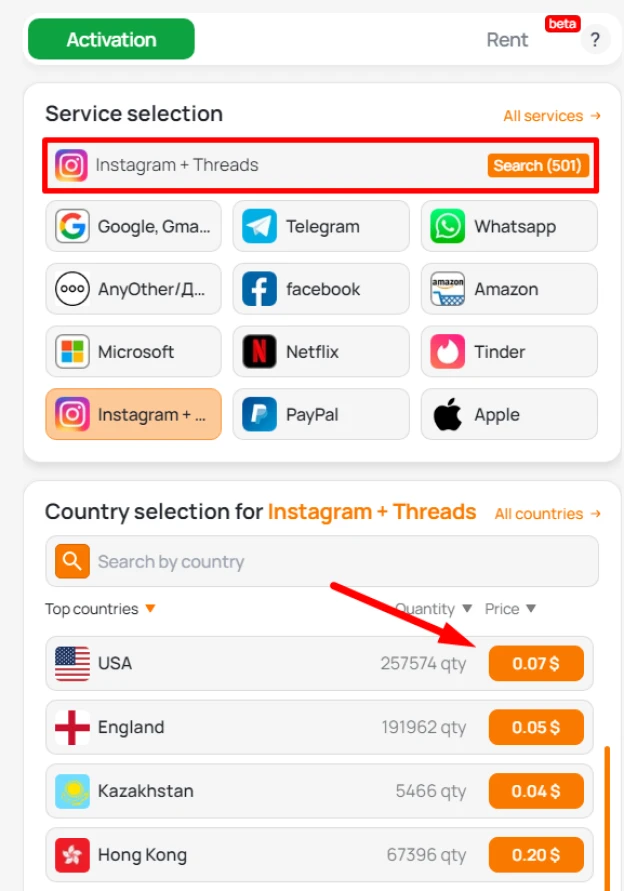
- Go directly to the social network site. As already noted, we do not need to buy an Instagram profile, but register it. Open the account creation window. Indicate a mobile phone as a verification method. Enter the virtual number purchased previously.
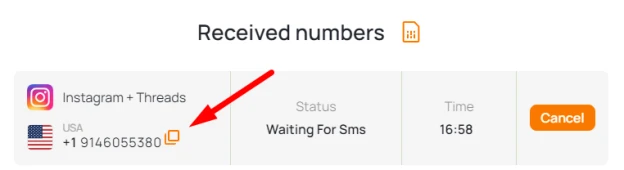
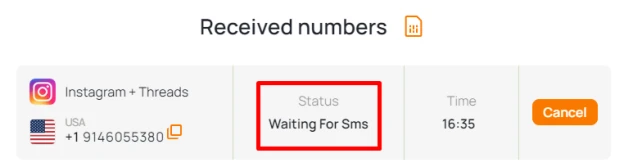
- Go back to the site "Grizzly Sms" to read the SMS. It is available in your account. Copy the six-digit code.
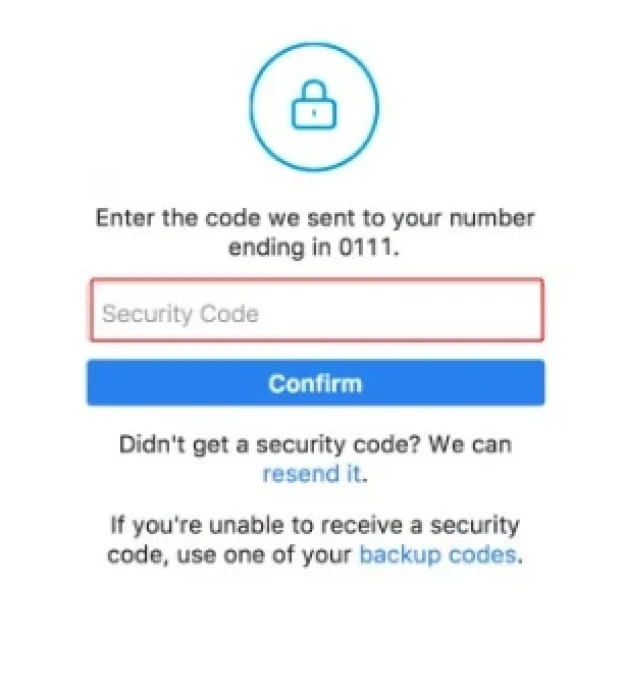
You get a ready-made profile that you can use at your discretion.
Why buying an Instagram account is not the best solution
You may ask why spend extra time on registration, if you can immediately buy a completely ready-made profile. There are several pitfalls that are not always thought about.
- Blocking. Buying a used Instagram account means attracting the attention of the security service. Algorithms identify similar profiles. As soon as suspicious activity occurs, they are banned.
- Reliability. Do you want to buy a female or male Instagram account? How safe is it, in terms of data protection? There are cases when, in pursuit of profit, the seller gives one number to several customers. Do not exclude the possibility of returning profiles.
- Prices. Given the above, the cost of purchasing ready profiles increases.
Registering a social network with a virtual number eliminates the described problems. The profile completely belongs to you and does not arouse suspicion of security algorithms.